Vous vous inquiétez des ravages qu'une attaque DDoS pourrait causer à votre cher serveur FiveM ? Plongez dans cet article pour comprendre les tenants et les aboutissants des attaques par déni de service distribué (DDoS) sur les serveurs FiveM. Non seulement nous dévoilerons les mécanismes de ces assauts malveillants, mais nous vous fournirons également une boîte à outils de stratégies visant à préserver l'intégrité de votre serveur.
Comprendre les attaques DDoS
Une attaque DDoS est une tentative malveillante de perturber le bon fonctionnement d'un serveur en l'inondant d'un torrent de trafic d'origines diverses. Dans le contexte d'un serveur FiveM, cet assaut peut entraîner des temps d'arrêt redoutés, la frustration des joueurs et des pertes financières potentielles pour les propriétaires de serveurs. Il est déconcertant de penser que si votre serveur s'arrête brusquement ou connaît des dysfonctionnements inexplicables, c'est qu'il est peut-être attaqué.
Les serveurs FiveM mettent souvent en œuvre des mesures de sécurité robustes pour atténuer l'impact des attaques DDoS. Ces mesures comprennent le filtrage avancé du trafic, l'équilibrage de la charge et les architectures de réseaux distribués. Si lancer une attaque DDoS contre un serveur FiveM peut sembler séduisant pour certains, le niveau de sophistication technique requis en fait une entreprise ardue. Les serveurs équipés de mécanismes de sécurité appropriés sont plus aptes à détourner de telles attaques, ce qui les rend moins vulnérables.
Vous souhaitez protéger votre serveur FiveM contre la tempête incessante d'une attaque DDoS ? Dans ce tutoriel étape par étape, nous vous fournirons des techniques efficaces pour contrecarrer les attaques DDoS et garantir un jeu ininterrompu à votre communauté.
Hébergement : Choisir un hébergeur protégé contre les attaques DDoS
L'une des mesures les plus importantes que vous pouvez prendre pour protéger votre serveur FiveM contre une attaque DDoS est de choisir un fournisseur d'hébergement protégé contre les attaques DDoS. Cela signifie que l'hébergeur a mis en œuvre des mesures pour détecter et atténuer les attaques DDoS avant qu'elles n'atteignent votre serveur.
Lors de la sélection d'un fournisseur d'hébergement, veillez à faire des recherches et à choisir un fournisseur qui a fait ses preuves en matière d'atténuation des attaques DDoS. En outre, recherchez un fournisseur qui propose des options d'hébergement évolutives, de sorte que vous puissiez facilement augmenter les ressources de votre serveur en fonction de l'augmentation du trafic.
OvH offre une bonne protection
Un bon hébergeur, bien connu, est OvH - il offre une protection DDoS prête à l'emploi. Consultez-le ici : https://www.ovhcloud.com/
Utiliser un pare-feu (payant)
L'introduction d'un pare-feu peut ériger une barrière solide contre les accès non autorisés et les attaques DDoS imminentes. Un pare-feu évalue de manière critique le trafic entrant et ne laisse passer que ce qui est légitime. Apprenez à déployer cet outil de sécurité à l'avantage de votre serveur, en réduisant considérablement les vulnérabilités.
Cloudflare

CloudflareCloudflare, un important réseau de diffusion de contenu (CDN), apparaît comme un allié exceptionnel dans votre lutte contre les attaques DDoS. En faisant appel à la protection de Cloudflare, vous pouvez repousser ces menaces de manière proactive et garantir un accès continu à vos joueurs. Embarquez dans un voyage pour activer la protection de Cloudflare, en l'intégrant de manière transparente dans votre serveur FiveM.
Bloquer tous les ports, sauf ceux dont vous avez besoin
Bloquer tous les ports sauf ceux de FiveM (et peut-être Teamspeak) :
- 30110 - (UDP/TCP) Serveur FiveM
- 30120 - (UDP/TCP) Serveur FiveM
- 9987 - (UDP) Teamspeak
Cela permet de bloquer de nombreuses attaques contre d'autres ports.
Pour configurer un pare-feu pour votre serveur FiveM, vous devrez utiliser un programme de pare-feu tel que Windows Firewall ou une solution de pare-feu tierce. Consultez la documentation du programme de pare-feu que vous avez choisi pour savoir comment le configurer pour votre serveur.
Surveiller le trafic et réagir rapidement
Dans un domaine où la vigilance règne en maître, surveillez attentivement les performances de votre serveur. Utilisez des outils de surveillance tels que Pingdom ou New Relic pour détecter les pics de trafic anormaux. La rapidité de réaction est essentielle ; identifiez immédiatement les attaques DDoS potentielles en examinant minutieusement les journaux de votre serveur. Face à l'adversité, envisagez la fermeture temporaire du serveur ou la transition vers un serveur de secours afin de préserver l'expérience de jeu de votre communauté.
Comment trouver l'adresse IP du serveur FiveM ?
FAQ
Peut-on faire un DDoS sur un serveur FiveM ?
Oui, il est techniquement possible de lancer une attaque DDoS contre un serveur FiveM. Il convient toutefois de souligner que les attaques DDoS sont des activités illégales ayant de graves implications juridiques. S'engager dans de telles actions peut conduire à des accusations criminelles et à des poursuites judiciaires, soulignant l'importance d'un comportement responsable en ligne. De plus, il convient de noter que les serveurs FiveM sont généralement plus résistants aux attaques DDoS que les serveurs de jeux classiques, ce qui rend de telles tentatives plus difficiles à exécuter efficacement.
Que signifie DDoS dans FiveM ?
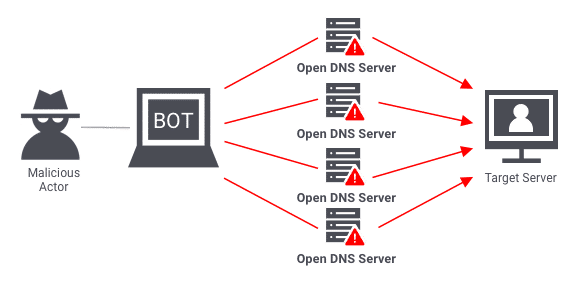
Le DDoS représente une forme puissante de cyberattaque visant les serveurs. Cette technique consiste à inonder le serveur cible d'une avalanche de trafic entrant provenant de nombreuses origines. Par conséquent, la capacité du serveur est mise à rude épreuve, conduisant à un effondrement potentiel sous l'immense pression. Les répercussions d’une attaque DDoS réussie peuvent être désastreuses, en particulier pour les entreprises qui dépendent fortement de leur présence en ligne pour générer des revenus.
Les mécanismes derrière les DDoS : Lorsqu’une attaque DDoS est exécutée, elle crée un embouteillage numérique. Les acteurs malveillants mobilisent stratégiquement une armée de dispositifs, souvent répartis dans le monde entier, pour envoyer simultanément un volume écrasant de requêtes au serveur cible. Résultat ? Les ressources du serveur sont épuisées alors qu'il s'efforce de traiter un nombre exorbitant de demandes. Ce déluge d'activité peut rapidement rendre le serveur inaccessible, entraînant une interruption des services et des retombées financières potentielles.
Conclusion
Atténuer une attaque DDoS sur votre serveur FiveM peut être une tâche difficile, mais en suivant ces étapes, vous pouvez réduire de manière significative l'impact d'une attaque et protéger votre serveur et vos joueurs. N'oubliez pas de choisir un fournisseur d'hébergement protégé contre les attaques DDoS, de mettre en place une liste blanche d'adresses IP, d'utiliser un pare-feu, d'activer la protection Cloudflare et de surveiller étroitement le trafic de votre serveur afin de réagir rapidement en cas d'attaque.
Tenez-vous informé des dernières menaces de sécurité et des meilleures pratiques pour protéger votre serveur FiveM, et n'hésitez pas à demander de l'aide à des experts ou à votre fournisseur d'hébergement si nécessaire. Avec la bonne approche et les bons outils, vous pouvez maintenir votre serveur en bon état de fonctionnement, même face à une attaque DDoS.