Are you worried about the havoc a DDoS attack could wreak on your cherished FiveM server? Dive into this article to understand the ins and outs of Distributed Denial of Service (DDoS) attacks on FiveM servers. Not only will we unravel the mechanics of these malicious assaults, but we’ll also arm you with a toolkit of strategies to safeguard your server’s sanctity.
Understanding DDoS Attacks
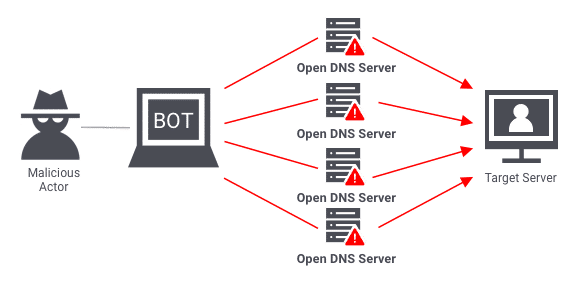
At the core of a DDoS attack is a malevolent endeavor to disrupt a server’s smooth operation by inundating it with a torrent of traffic from diverse origins. In the context of a FiveM server, this onslaught can lead to dreaded downtimes, player frustration, and the perilous potential for financial losses among server owners. It’s unnerving to consider that if your server abruptly exits or experiences inexplicable glitches, it might be under attack.
FiveM servers often implement robust security measures to mitigate the impact of DDoS attacks. These measures include advanced traffic filtering, load balancing, and distributed network architectures. While launching a DDoS attack against a FiveM server may seem enticing to some, the level of technical sophistication required makes it an arduous endeavor. Servers equipped with proper security mechanisms are more adept at deflecting such attacks, rendering them less vulnerable.
Worried about safeguarding your FiveM server from the relentless storm of a DDoS attack? In this step-by-step tutorial, we’ll arm you with effective techniques to thwart DDoS attacks and ensure uninterrupted gameplay for your community.
Hosting: Choose a DDoS Protected Host
One of the most important steps you can take to protect your FiveM server from a DDoS attack is to choose a DDoS protected hosting provider. This means that the hosting provider has implemented measures to detect and mitigate DDoS attacks before they can reach your server.
When selecting a hosting provider, be sure to do your research and choose a provider that has a proven track record of successfully mitigating DDoS attacks. Additionally, look for a provider that offers scalable hosting options, so you can easily upgrade your server resources as needed to handle increased traffic.
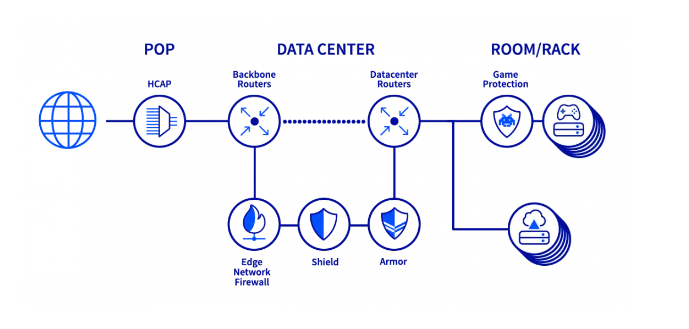
OvH offers a good protection
A good, well known hoster, is OvH – it offers a DDoS protection out-of-the-box. Check it out here: https://www.ovhcloud.com/
Use a (paid) Firewall
Introducing a firewall can erect a sturdy barrier against unauthorized access and impending DDoS assaults. A firewall critically evaluates incoming traffic, allowing only the legitimate through. Learn how to expertly deploy this security tool to your server’s advantage, significantly reducing vulnerabilities.
Cloudflare

Cloudflare, a prominent content delivery network (CDN), emerges as an exceptional ally in your fight against DDoS attacks. By enlisting Cloudflare’s protective embrace, you can proactively fend off these threats, ensuring continuous accessibility for your players. Embark on a journey to enable Cloudflare protection, seamlessly integrating it into your FiveM server.
Block all ports, except the ones you need
Block all ports except those for FiveM (and maybe Teamspeak):
- 30110 – (UDP/TCP) FiveM server
- 30120 – (UDP/TCP) FiveM server
- 9987 – (UDP) Teamspeak
This helps to block many attacks against other ports.
To set up a firewall for your FiveM server, you’ll need to use a firewall program such as Windows Firewall or a third-party firewall solution. Consult the documentation for your chosen firewall program for instructions on how to configure it for your server.
Monitor Traffic and React Quickly
In a realm where vigilance reigns supreme, monitor your server’s performance vigilantly. Employ monitoring tools like Pingdom or New Relic to detect abnormal spikes in traffic. Swift response is key; immediately identify potential DDoS attacks by scrutinizing your server logs. In the face of adversity, consider temporary server shutdown or transition to a backup server to safeguard your community’s gameplay experience.
How to find out FiveM Server IP Address
FAQ
Can you DDoS a FiveM server?
Yes, it is technically possible to launch a DDoS attack against a FiveM server. However, a critical point to emphasize is that DDoS attacks are unlawful activities with severe legal implications. Engaging in such actions can lead to criminal charges and legal actions, underscoring the importance of responsible online behavior. Moreover, it’s worth noting that FiveM servers are typically more resilient to DDoS attacks compared to regular game servers, making such attempts more challenging to execute effectively.
What does DDoS mean in FiveM?
DDoS represents a potent form of cyber assault aimed at servers. This technique involves inundating the target server with an avalanche of incoming traffic sourced from numerous origins. Consequently, the server’s capacity becomes strained, leading to potential collapse under the immense strain. The repercussions of a successful DDoS attack can be dire, especially for enterprises heavily reliant on their online presence for revenue generation.
The Mechanics Behind DDoS: When a DDoS attack is executed, it’s creating a digital traffic jam. Malicious actors strategically marshal an army of devices, often spanning the globe, to simultaneously send an overwhelming volume of requests to the target server. The result? The server’s resources are depleted as it grapples with processing an exorbitant number of demands. This deluge of activity can swiftly render the server inaccessible, leading to a disruption of services and potential financial fallout.
Conclusion
Mitigating a DDoS attack on your FiveM server can be a challenging task, but by following these steps, you can significantly reduce the impact of an attack and protect your server and players. Remember to choose a DDoS protected hosting provider, implement IP whitelisting, use a firewall, enable Cloudflare protection, and monitor your server’s traffic closely to react quickly if an attack occurs.
Stay informed about the latest security threats and best practices for protecting your FiveM server, and don’t hesitate to seek help from experts or your hosting provider if needed. With the right approach and tools, you can keep your server up and running smoothly, even in the face of a DDoS attack.